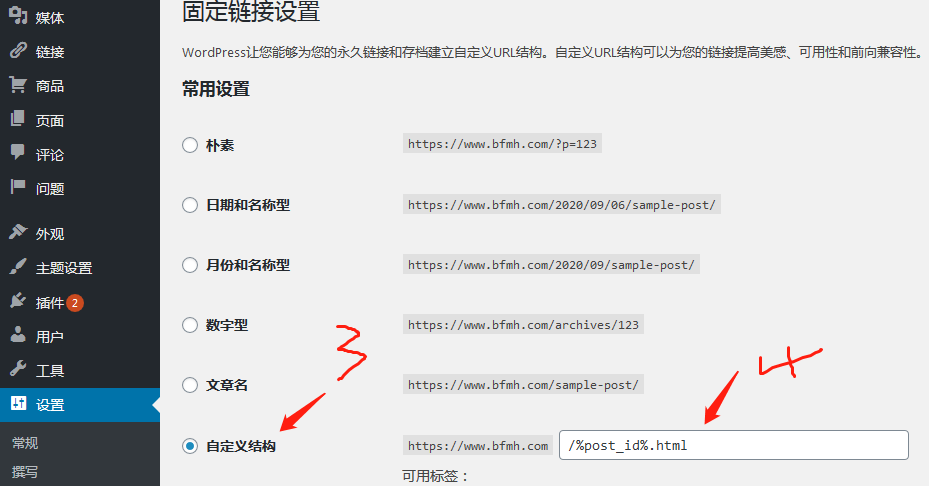
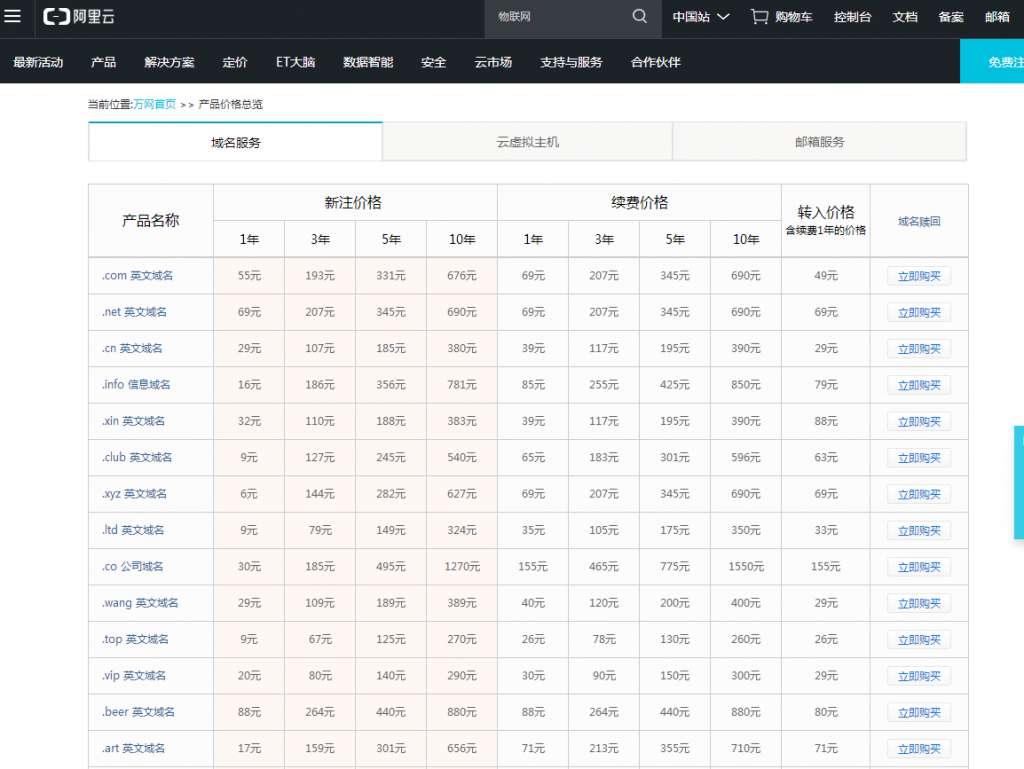
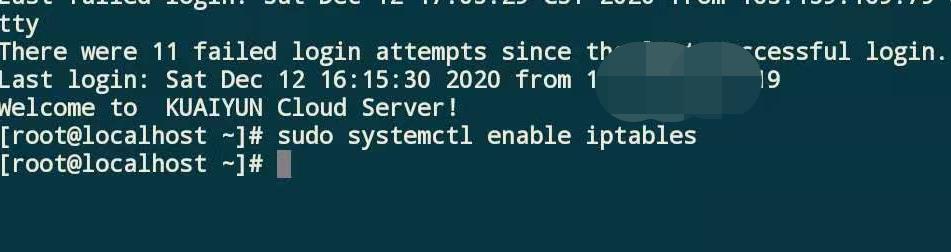
 CentOS 7默认一般为firewall防火墙,分享一下如何改成iptables防火墙:
CentOS 7默认一般为firewall防火墙,分享一下如何改成iptables防火墙:
1.关闭防火墙:sudo systemctl stop firewalld.service
systemctl start firewalld.service #启动firewall
systemctl stop firewalld.service #停止firewall(选这个停止命令)
systemctl disable firewalld.service #禁止firewall开机启动
2. 关闭开机启动:sudo systemctl disable firewalld.service
3.安装iptables防火墙命令:sudo yum install iptables-services
4.配置iptables防火墙 打开指定端口 (可自己网上收集)
5. 设置iptables防火墙开机启动命令:sudo systemctl enable iptables
6 修改防火墙配置文件 进入服务器 /etc/sysconfig/iptables 编辑 iptables 文件(先备份此文件,不行可以还原
6.1编辑iptables配置文件,将文件内容更改为如下,则具备了ip地址白名单功能
#vim /etc/sysconfig/iptables
les
代码如下
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-N whitelist
-A whitelist -s 1.2.3.4/24 -j ACCEPT
-A whitelist -s 2.3.4.5 -j ACCEPT
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 22 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 8080 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 80 -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
6~8 行是添加白名单列表,可以是ip段或者单个ip地址
10~12行 注意的是“-j whitelist”而不是“-j ACCEPT”,前者将该端口访问权限限制在白名单内,后者为不限制
13行 任何ip地址都能ping通该主机,因为“-j ACCEPT”没有做相应限制
配置完毕后,运行命令重启防火墙使规则生效
#systemctl restart iptables.service
因我服务器用了360网站卫士CDN云防护和百度云CDN网站,找到对应放行的IP段如下(可按自己实际需求设置)
代码如下
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-N whitelist
-A whitelist -s 36.27.212.0/255 -j ACCEPT
-A whitelist -s 123.129.232.0/255 -j ACCEPT
-A whitelist -s 119.188.9.0/24 -j ACCEPT
-A whitelist -s 42.236.93.0/24 -j ACCEPT
-A whitelist -s 220.170.185.0/24 -j ACCEPT
-A whitelist -s 115.231.186.0/25 -j ACCEPT
-A whitelist -s 183.232.51.0/24 -j ACCEPT
-A whitelist -s 61.182.137.0/25 -j ACCEPT
-A whitelist -s 112.25.90.0/24 -j ACCEPT
-A whitelist -s 59.51.81.128/191 -j ACCEPT
-A whitelist -s 222.216.190.0/24 -j ACCEPT
-A whitelist -s 122.190.2.0/24 -j ACCEPT
-A whitelist -s 125.39.239.0/24 -j ACCEPT
-A whitelist -s 183.61.177.0/24 -j ACCEPT
-A whitelist -s 183.61.236.0/24 -j ACCEPT
-A whitelist -s 124.95.168.128/191 -j ACCEPT
-A whitelist -s 124.95.191.0/24 -j ACCEPT
-A whitelist -s 58.211.2.0/24 -j ACCEPT
-A whitelist -s 117.34.13.0/24 -j ACCEPT
-A whitelist -s 150.138.150.0/24 -j ACCEPT
-A whitelist -s 150.138.149.128/25 -j ACCEPT
-A whitelist -s 157.255.25.0/24 -j ACCEPT
-A whitelist -s 113.207.101.0/25 -j ACCEPT
-A whitelist -s 111.32.135.0/25 -j ACCEPT
-A whitelist -s 42.81.6.0/25 -j ACCEPT
-A whitelist -s 115.231.187.148 -j ACCEPT
-A whitelist -s 58.211.137.148 -j ACCEPT
-A whitelist -s 117.34.14.148 -j ACCEPT
-A whitelist -s 125.39.174.148 -j ACCEPT
-A whitelist -s 42.236.94.148 -j ACCEPT
-A whitelist -s 113.207.102.148 -j ACCEPT
-A whitelist -s 122.190.3.148 -j ACCEPT
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 20 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 21 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 22 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 1521 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 80 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 8080 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 3306 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 443 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 53 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 465 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 25 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 110 -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
 北方门户
北方门户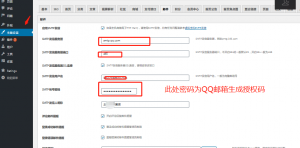 2.QQ邮箱设置界面,可生成授权码,供步骤1使用。
2.QQ邮箱设置界面,可生成授权码,供步骤1使用。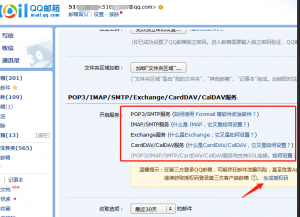
 1.2域名解析设置页面 不知道是不是多了解析,可以自己测试哦反正我的就是这个设置。百度云加速设置如图三图四
1.2域名解析设置页面 不知道是不是多了解析,可以自己测试哦反正我的就是这个设置。百度云加速设置如图三图四
 2.1,运行CMD ping下带WWW和不带WWW的是不是已经变成百度加速后撤了,图五为解析成功
2.1,运行CMD ping下带WWW和不带WWW的是不是已经变成百度加速后撤了,图五为解析成功

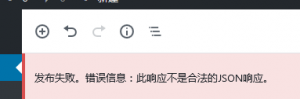
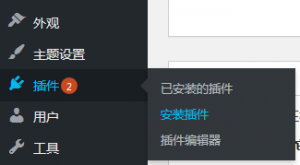 2.搜索插件Classic Editor,(其实我安装的是箭头的那个一样测试安装后启动默认设置后,可以发布文章)
2.搜索插件Classic Editor,(其实我安装的是箭头的那个一样测试安装后启动默认设置后,可以发布文章)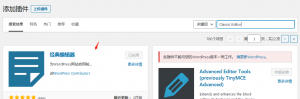 3.安装完成后启动,用默认设置即可,测试可以正常发布文章了哦。
3.安装完成后启动,用默认设置即可,测试可以正常发布文章了哦。